People change jobs.
Make sure your data doesn’t go with them.
Avoid data loss surprises as a result of employee departures. Detect, investigate and respond before damage is done.

Get real protection from insider threats
Odds are, you’re experiencing an insider threat right now. Here are the most common times when employees put data at risk:
-
Learn More
Employee Departure
Most employees take data with them when they leave for their next job. We make sure your most valuable files stay with you.
-
Learn More
Mergers & Acquisitions
M&A deals often trigger employee turnover and layoffs. We keep your data protected during the transition.
-
Learn More
High-Value Data Leak
There are files that will damage your business if leaked. We help you quickly detect when that information is put at risk.

Collect and Monitor
Automatically monitor all file activity across endpoints and cloud.
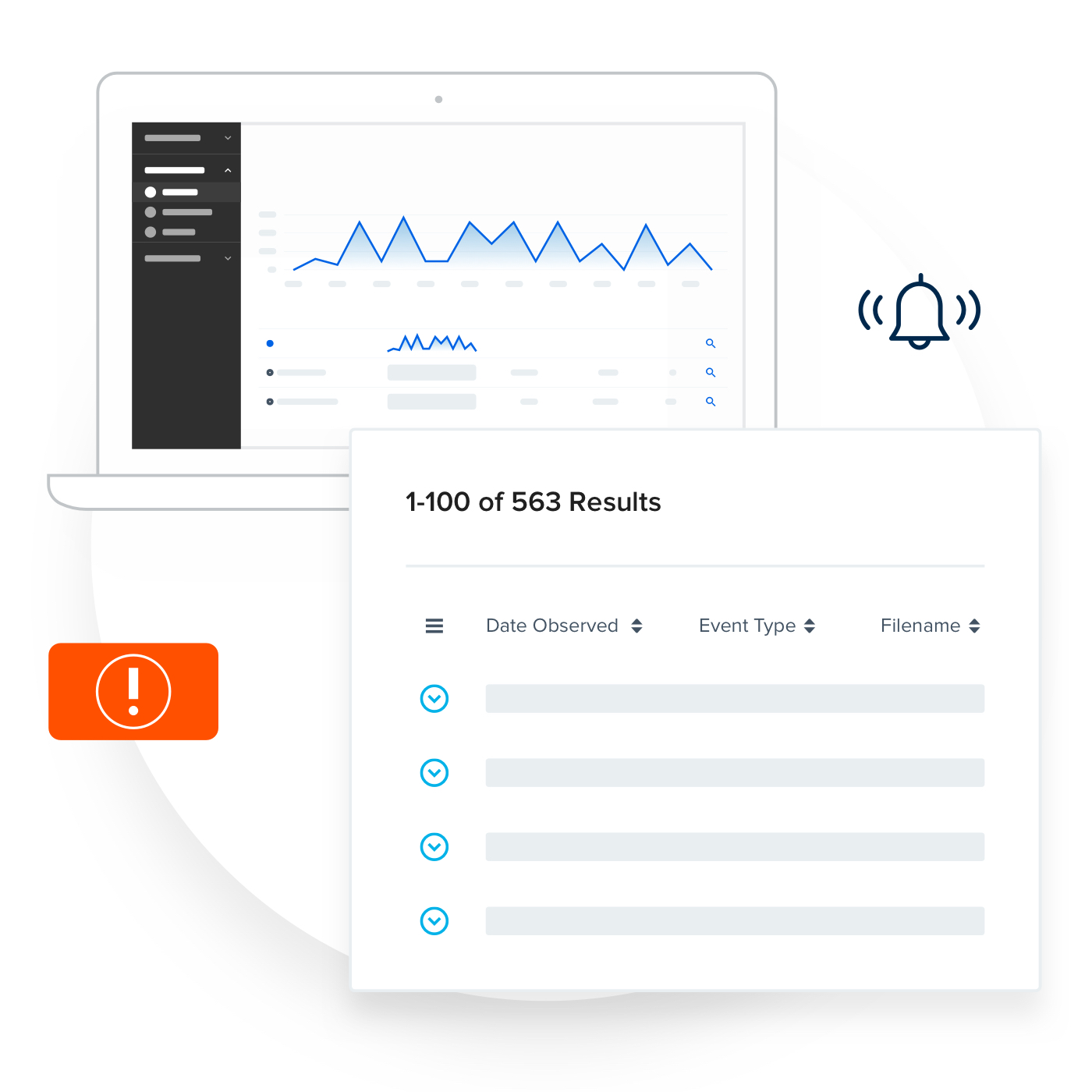
Detect and Investigate
Easily detect suspicious use of USB, browsers and cloud services.
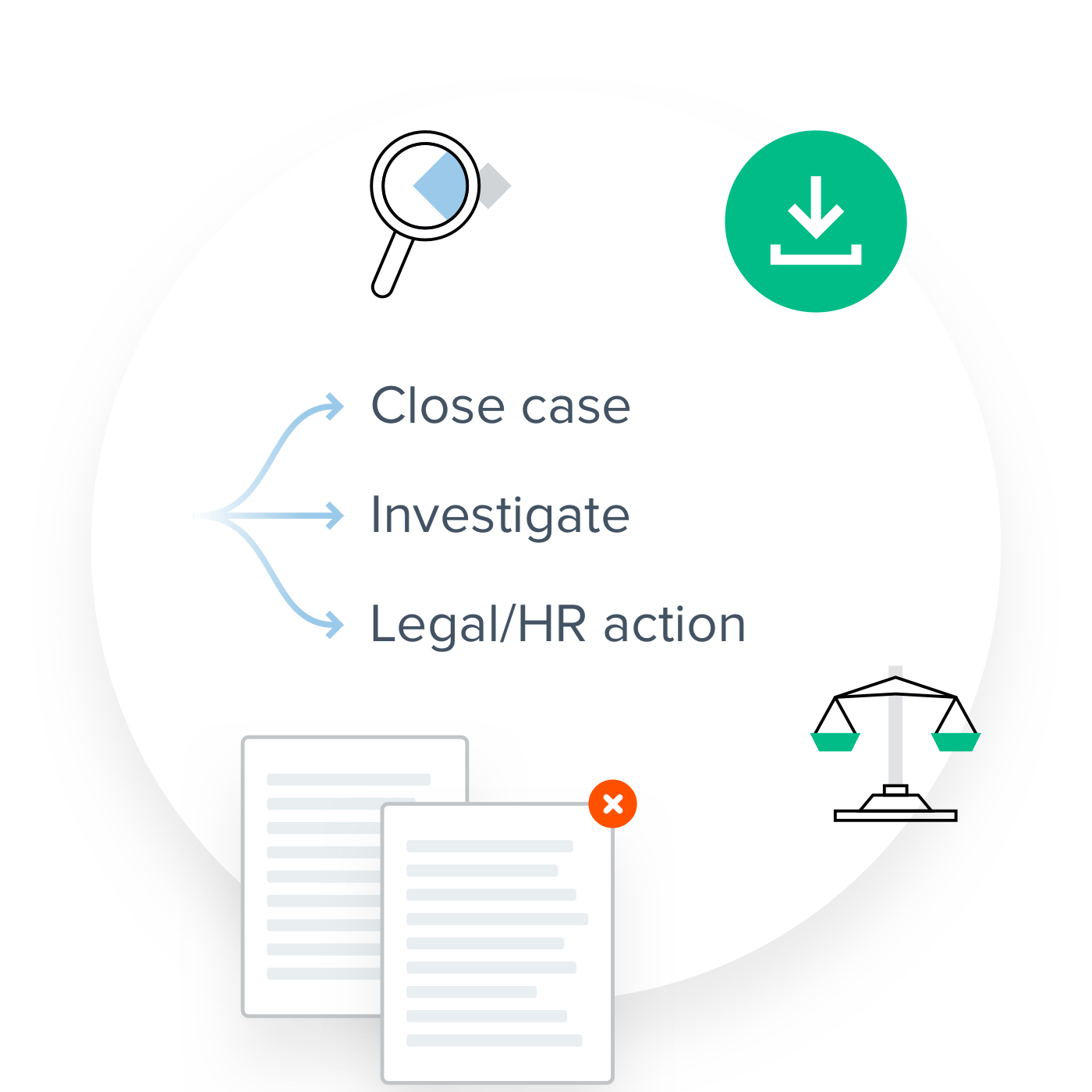
Assess and Respond
Quickly investigate data, recover files and respond to real risk.
Recognized for Excellence
Learn more about code42
Frequently Asked Questions
What types of removable media devices do you monitor?
Devices, such as flash drives, hard drives and cards, that connect via USB, eSata, Thunderbolt and SD Card ports. Code42 collects the vendor, name and serial number of all devices used.
What web browsers and applications do you monitor?
Internet Explorer, Chrome, Firefox, Safari, Edge, Chromium and Opera, as well as processes/applications such as FileZilla, Winscp, Slack, SFTP, FTP, Curland SCP.
What cloud applications do you monitor?
Does Code42 use an endpoint agent?
Yes, Code42 uses a non-disruptive agent installed on Windows, Mac and Linux devices to monitor file activity as well as collect files and file metadata. Maximum CPU allowances can be set for when users are present and away from their devices.
How do you identify when important files are put at risk?
Customizable alerts can be set for near real-time notification of risky activity. Code42 assigns categories to files in order to help you identify your most important data at a glance. Monitored categories include archive, audio, document, executable, image, PDF, presentation, script, source code, spreadsheet, video and virtual disk image. When you’re alerted of risk, you can quickly access the file(s) in question to make an informed decision about whether that file needs to remain private. Finally, most organizations further narrow their focus by prioritizing alerting during times where data is put at the most risk, such as during employee departure and M&A.
What web browsers and applications do you monitor?
Internet Explorer, Chrome, Firefox, Safari, Edge, Chromium and Opera, as well as processes/applications such as FileZilla, Winscp, Slack, SFTP, FTP, Curland SCP.
What types of removable media devices do you monitor?
Devices, such as flash drives, hard drives and cards, that connect via USB, eSata, Thunderbolt and SD Card ports. Code42 collects the vendor, name and serial number of all devices used.
How do you identify when important files are put at risk?
Customizable alerts can be set for near real-time notification of risky activity. Code42 assigns categories to files in order to help you identify your most important data at a glance. Monitored categories include archive, audio, document, executable, image, PDF, presentation, script, source code, spreadsheet, video and virtual disk image. When you’re alerted of risk, you can quickly access the file(s) in question to make an informed decision about whether that file needs to remain private. Finally, most organizations further narrow their focus by prioritizing alerting during times where data is put at the most risk, such as during employee departure and M&A.
What cloud applications do you monitor?
Does Code42 use an endpoint agent?
Yes, Code42 uses a non-disruptive agent installed on Windows, Mac and Linux devices to monitor file activity as well as collect files and file metadata. Maximum CPU allowances can be set for when users are present and away from their devices.
What cloud applications do you monitor?
What types of removable media devices do you monitor?
Devices, such as flash drives, hard drives and cards, that connect via USB, eSata, Thunderbolt and SD Card ports. Code42 collects the vendor, name and serial number of all devices used.
Does Code42 use an endpoint agent?
Yes, Code42 uses a non-disruptive agent installed on Windows, Mac and Linux devices to monitor file activity as well as collect files and file metadata. Maximum CPU allowances can be set for when users are present and away from their devices.
How do you identify when important files are put at risk?
Customizable alerts can be set for near real-time notification of risky activity. Code42 assigns categories to files in order to help you identify your most important data at a glance. Monitored categories include archive, audio, document, executable, image, PDF, presentation, script, source code, spreadsheet, video and virtual disk image. When you’re alerted of risk, you can quickly access the file(s) in question to make an informed decision about whether that file needs to remain private. Finally, most organizations further narrow their focus by prioritizing alerting during times where data is put at the most risk, such as during employee departure and M&A.
What cloud applications do you monitor?
What types of removable media devices do you monitor?
Devices, such as flash drives, hard drives and cards, that connect via USB, eSata, Thunderbolt and SD Card ports. Code42 collects the vendor, name and serial number of all devices used.
What web browsers and applications do you monitor?
Internet Explorer, Chrome, Firefox, Safari, Edge, Chromium and Opera, as well as processes/applications such as FileZilla, Winscp, Slack, SFTP, FTP, Curland SCP.
What types of removable media devices do you monitor?
Devices, such as flash drives, hard drives and cards, that connect via USB, eSata, Thunderbolt and SD Card ports. Code42 collects the vendor, name and serial number of all devices used.
How do you identify when important files are put at risk?
Customizable alerts can be set for near real-time notification of risky activity. Code42 assigns categories to files in order to help you identify your most important data at a glance. Monitored categories include archive, audio, document, executable, image, PDF, presentation, script, source code, spreadsheet, video and virtual disk image. When you’re alerted of risk, you can quickly access the file(s) in question to make an informed decision about whether that file needs to remain private. Finally, most organizations further narrow their focus by prioritizing alerting during times where data is put at the most risk, such as during employee departure and M&A.
What cloud applications do you monitor?
Does Code42 use an endpoint agent?
Yes, Code42 uses a non-disruptive agent installed on Windows, Mac and Linux devices to monitor file activity as well as collect files and file metadata. Maximum CPU allowances can be set for when users are present and away from their devices.
















